
[ad_1]
Home windows working techniques are the goal of new malware dubbed ZenRAT by U.S.-based cybersecurity firm Proofpoint. The attackers constructed a web site that impersonates the favored Bitwarden password supervisor; if accessed by way of Home windows, the faux web site delivers the ZenRAT malware disguised as Bitwarden software program. It’s at the moment unknown if the malware is utilized by risk actors for cyberespionage or for monetary fraud.
We’ll delve into the technical particulars and share extra info from Proofpoint researchers, in addition to present tips about mitigating this ZenRAT malware risk.
Leap to:
What’s ZenRAT malware, and what occurs when it’s executed?
ZenRAT is malware developed in .NET. It was beforehand unreported and particularly targets Microsoft Home windows working techniques. As soon as executed, the ZenRAT malware queries the system to assemble info:
- CPU and GPU names.
- Working system model.
- RAM capabilities.
- IP handle and gateway IP handle.
- Put in software program together with antivirus.
The info is shipped as a ZIP archive file to its command and management server, together with stolen browser knowledge and credentials. The ZIP file incorporates two information named InstalledApps.txt and SysInfo.txt. Proofpoint informed TechRepublic that they ” … noticed ZenRAT stealing knowledge from each Chrome and Firefox” and imagine “It’s cheap to imagine that it might have assist for many Chromium-based browsers.”
The malware executes a number of checks when operating. For starters, it checks that it doesn’t function from Belarus, Kyrgyzstan, Kazakhstan, Moldova, Russia or Ukraine.
Then, the malware ensures it doesn’t already run on the system by checking for a particular mutex and that the laborious drive isn’t lower than 95GB in dimension, which could point out a sandbox system to the malware. It additionally checks for recognized virtualization merchandise’ course of names to confirm it isn’t operating in a virtualized surroundings.
As soon as the checks have been handed, the malware sends a ping command to make certain it’s related to the web, and checks if there’s an replace for the malware.
As well as, the malware has the flexibility to ship its log information to the C2 server in clear textual content, in all probability for debugging functions, though all the opposite communications are encrypted.
ZenRAT pretends to be a Bitwarden password supervisor bundle
Attackers have constructed a web site bitwariden[.]com that impersonates the favored Bitwarden password supervisor. The web site is a really convincing copy of the legit web site from Bitwarden (Determine A).
Determine A
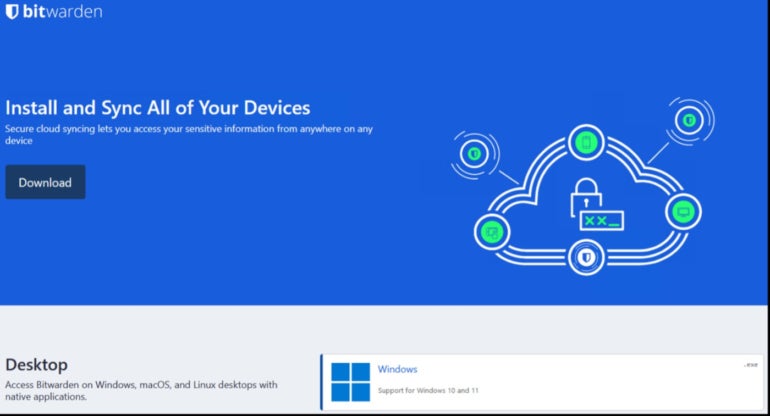
If accessed by way of a Home windows working system, the faux web site delivers the ZenRAT malware disguised as Bitwarden software program. If a non-Home windows system person browses the web site, the content material is totally totally different, and the person is proven an article copied from opensource.com about Bitwarden Password Supervisor.
If a Home windows person clicks on the Linux or Mac obtain hyperlink for Bitwarden, they’re redirected to the legit obtain pages from Bitwarden.
After a Home windows person clicks the obtain hyperlink from the faux web site, a file named Bitwarden-Installer-version-2023-7-1.exe is downloaded from one other area, crazygameis[.]com, which isn’t accessible anymore.
The malicious installer was first reported on the VirusTotal platform on July 28, 2023 but below a special identify: CertificateUpdate-version1-102-90. This would possibly point out that there could have been a earlier an infection marketing campaign during which attackers might need triggered one other social engineering trick based mostly on certificates.
The metadata for the file incorporates bogus info. The installer claims to be Piriform’s Speccy, a software program utility for gathering techniques specs. It additionally claims to be signed by Tim Kosse, a developer well-known for the FileZilla FTP/SFTP software program, however the file signature is invalid.
Once we requested Proofpoint’s Risk Analysis group about why the attacker didn’t change the metadata to suit the Bitwarden utility higher, they mentioned “It’s attainable the actor was lazy, or simply didn’t need to hassle with altering it. Many shoppers don’t take note of these particulars. If the filename appears proper, they’ll in all probability execute it with out questioning file metadata or digital signatures.”
As soon as launched, the installer creates a duplicate of itself into the AppDataLocalTemp folder of the at the moment logged-in person. It additionally creates a hidden file named .cmd in the identical folder. The .cmd file deletes the installer and itself utilizing a command line loop. An executable file named ApplicationRuntimeMonitor.exe is positioned into the person’s AppDataRoamingRunTimeMonitor folder earlier than being executed.
ZenRAT has been designed to be modular, though Proofpoint didn’t see further modules. It’s anticipated that extra modules is likely to be developed and applied with ZenRAT sooner or later.
How one can defend from this ZenRAT malware risk
Proofpoint indicated it’s not recognized how the malware is being distributed; nevertheless, hyperlinks to the faux Bitwarden web site are in all probability despatched to targets by way of e mail, social networks, immediate messaging, by way of faux advertisements or search engine optimisation poisoning.
As famous by Proofpoint, folks needs to be cautious of advertisements in search engine outcomes, as a result of it appears to be a significant driver of infections of this nature, particularly inside the final 12 months.
It’s suggested to deploy safety options which might be in a position to analyze e mail hyperlinks and hooked up information, along with safety options monitoring endpoints and servers.
Working techniques and all software program operating on it ought to at all times be saved updated and patched to keep away from being compromised by a typical vulnerability.
Customers also needs to be cautious of invalid digital certificates when operating an executable file that has a nonvalid digital signature. Present Microsoft Home windows techniques are configured by default to alert customers about such a file earlier than executing it. When unsure, customers shouldn’t execute the file and ask their IT workers about it.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.
[ad_2]